Global cyber attack hits businesses who fail to patch their systems
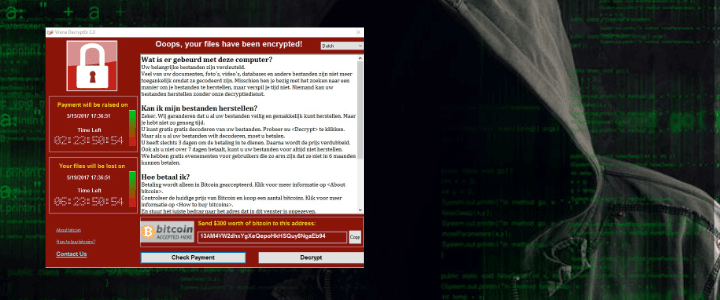
As the repercussions of the WannaCry (or WannaCrypt) RansomWare attack continues this week, it once again highlights the risks cyber attacks pose to businesses around the globe.
There are now over 200,000 computers in 150 countries known to have been affected.
Governments, hospitals and major companies have all found themselves battling the malware, which demands money in return for unfreezing computers. Many firms have had experts working over the weekend to prevent new infections. The virus took control of users’ files and demanded $300 (£230) payment to restore access. In Russia the Interior Ministry was worst hit, while in France car manufacturer Renault had to cease production. In China, computers at nearly 30,000 institutions and organisations were affected, including government agencies and hospitals.
Worst hit in the UK was the NHS (National Health Service) which runs hospitals and doctors surgeries. It appears some hospitals were still using outdated systems. The government told NHS trusts in 2014 that they needed to move away from Windows XP as rapidly as possible. Having said that, some of the more recent Windows versions also suffered from the same vulnerability.
WannaCrypt used an exploit originally developed by the US National Security Agency (NSA) before it was leaked by hacking group, the Shadow Brokers, last month. The WannaCrypt ransomware relies on a recently patched vulnerability in Microsoft’s SMB file-sharing services (MS17-010).
Microsoft had released a set of security patches as part of the critical Security Bulletin MS17-010 on 14th March 2017 that can effectively prevent the spread of this ransomware. Unfortunately many organisations find it difficult to maintain their systems up to date, in a timely manner. Even a few vulnerable devices are sufficient to compromise the whole organisation.
A 22-year-old UK security researcher “accidentally” halted the spread of the malicious ransomware. Known by the pseudonym MalwareTech, he managed to find what appeared to be a “kill switch” in the rogue software’s code by registering a web domain (iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com) that the malware attempted to connect to.
Several variants of the WannaCrypt malware have been already been spotted and these have also been stopped via a similar kill switch. But it may not be long before the next attempt, and this may not be so easy to stop.
How you can reduce the risk of cyber attack
- Install Windows Updates (the patch for this vulnerability had been released in March)
- Don’t download attachments or click links in emails you don’t recognise.
- Backup your systems regularly.
- Use Endpoint security and keep it up to date.
How can AP help reduce your risk of attack
As a partner of Nexthink we can help customers to ensure that effective security-operations measures are maintained across your business. Nexthink can help the security and compliance teams adopt proactive measures to avoid propagation of new attacks.
- Identifying all outdated endpoint and server operating systems.
- Ensuring all end-points have working and updated protection solutions.
- Monitoring activities such as shadow IT communications, existence of TOR software, communications over SMB ports to multiple devices.
- Getting alerted when detecting the existence of dangerous activities such as high threat binaries, anomalous traffic patterns.
Nexthink customers can download the recently released “WannaCry vulnerability test” library which will identify all devices that are potentially subject to the WannaCry ransomware. This pack can be installed in just a few seconds and does not require any configuration.
And you can also find out more about how Nexthink can help prevent such attacks at your organisation by tuning into this webinar:
Register for the WannaCry Webinar
Title : Are you vulnerable to WannaCry?
Presenter : Matthew Aylard – Security Expert at Nexthink
Date: Wednesday 17 May – 4pm BST / 11am EST
Description :
- Do you understand the risks?
- What could we have done as IT professionals?
- What happens once the virus evolves… WannaCry 2.0?
https://register.gotowebinar.com/register/3414107132229054467

